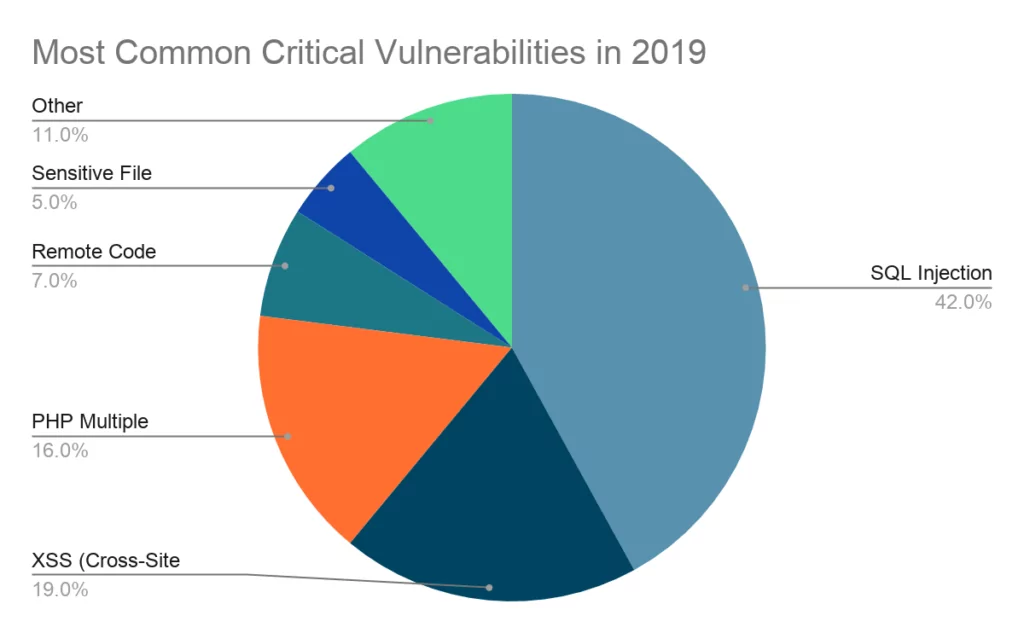
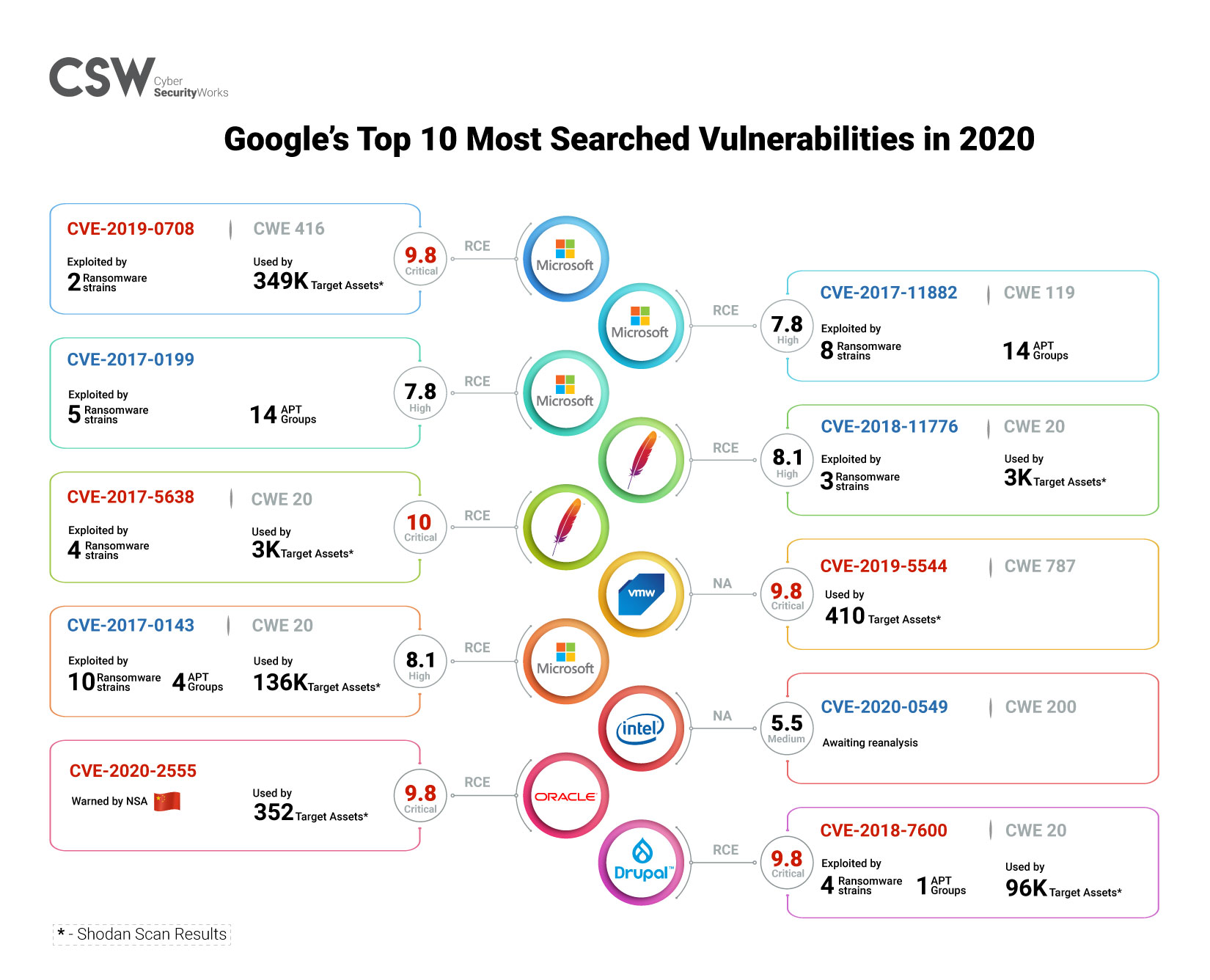
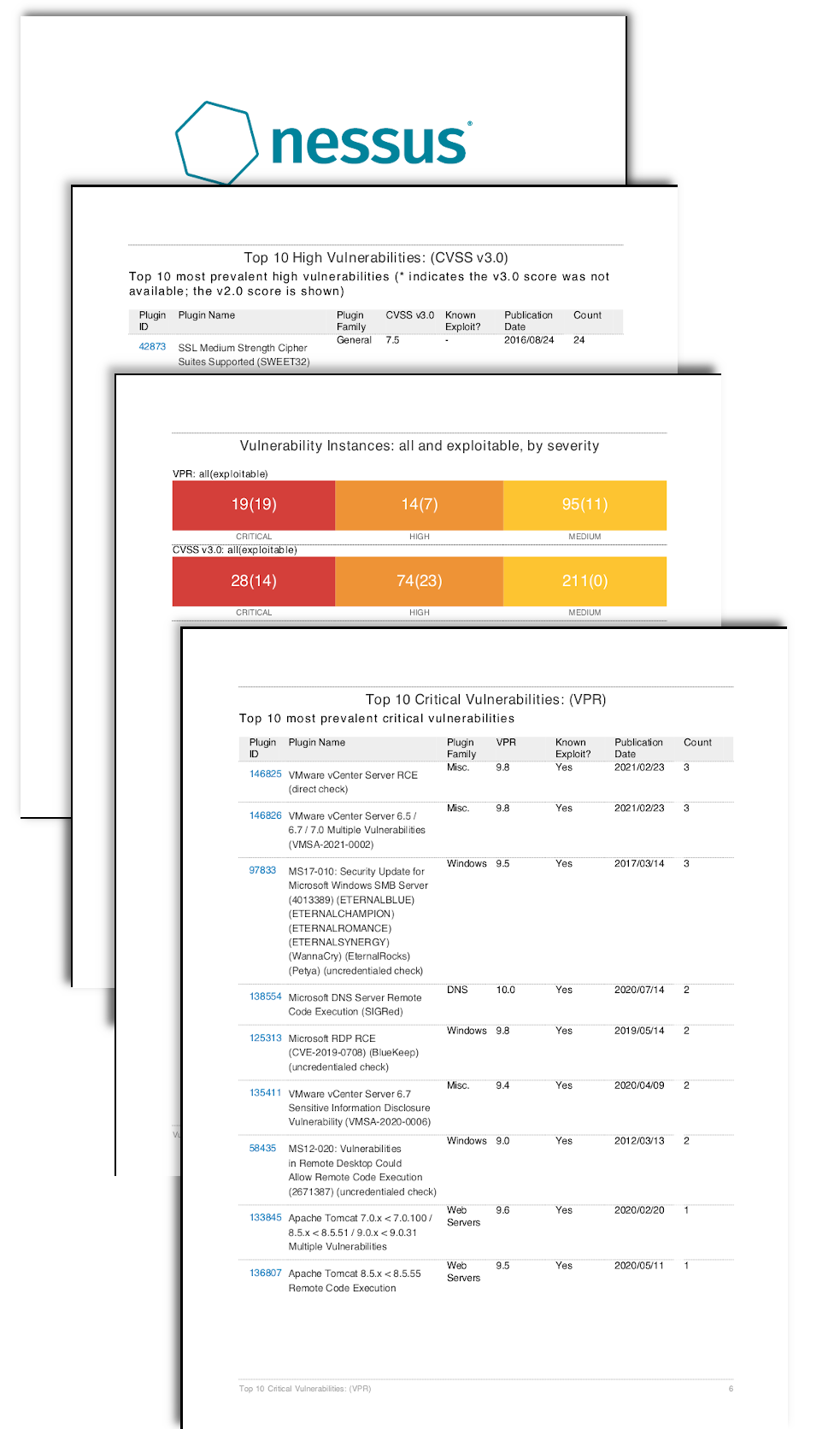
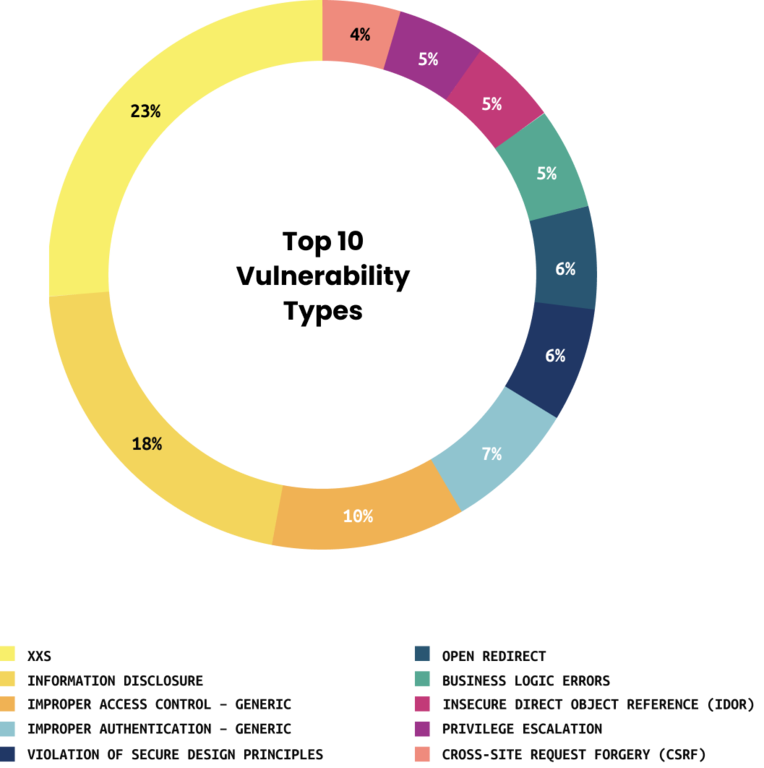
The Top 10 Vulnerabilities Used by Cybercriminals in 2019 | Recorded Future - Journal of Cyber Policy

2019 Cybersecurity Insights -4 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.