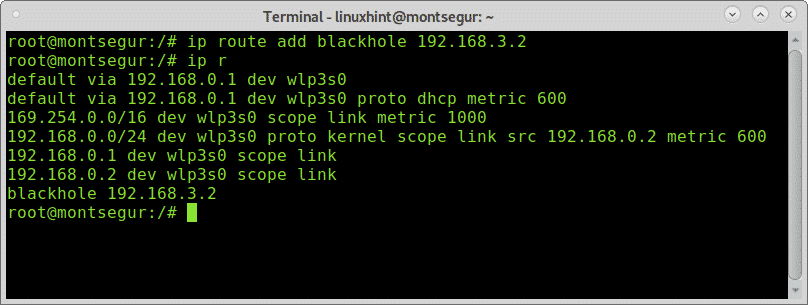
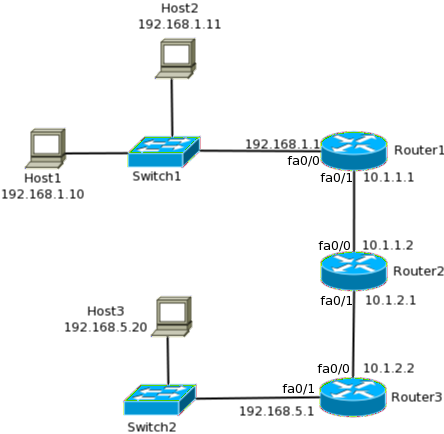
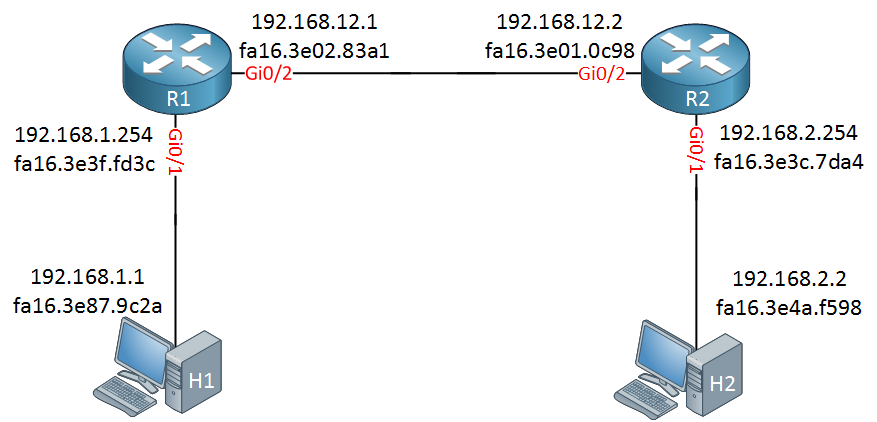
![IP Addressing: NAT Configuration Guide - Configuring NAT for IP Address Conservation [Cisco ASR 1000 Series Aggregation Services Routers] - Cisco IP Addressing: NAT Configuration Guide - Configuring NAT for IP Address Conservation [Cisco ASR 1000 Series Aggregation Services Routers] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/100001-200000/120001-130000/127001-128000/127011.ps/_jcr_content/renditions/127011.jpg)
IP Addressing: NAT Configuration Guide - Configuring NAT for IP Address Conservation [Cisco ASR 1000 Series Aggregation Services Routers] - Cisco

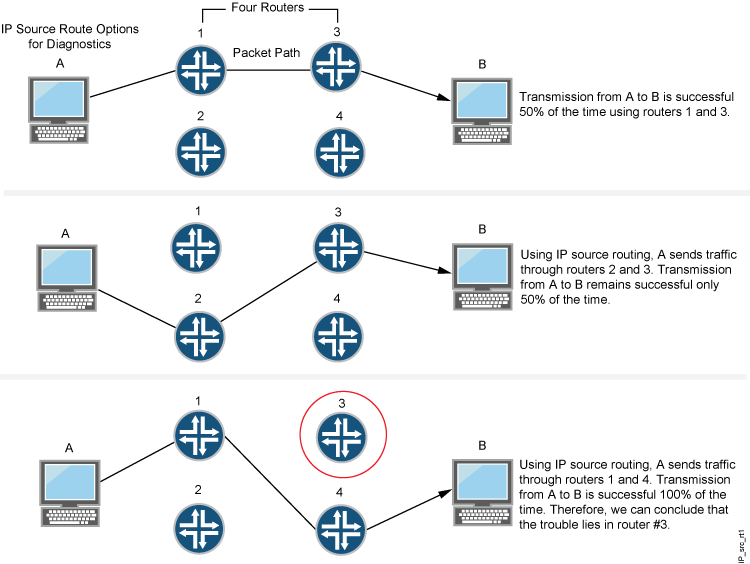
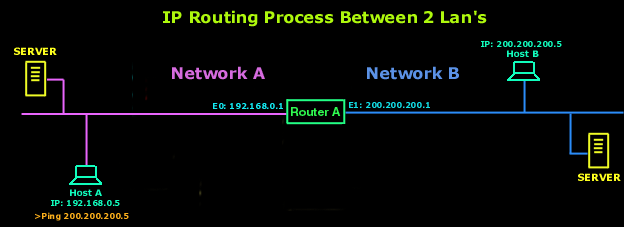
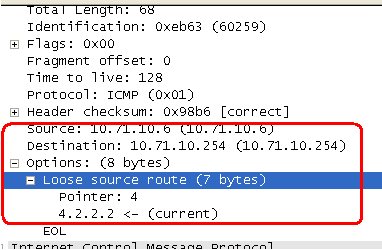
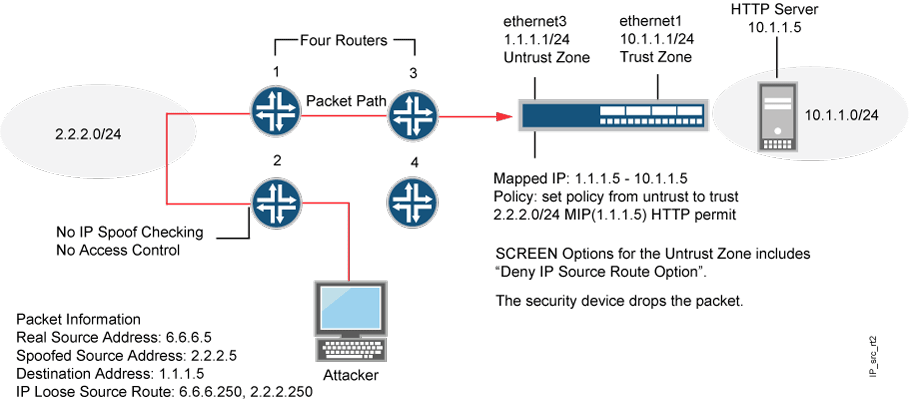
8.5 IP Source Routing Option | TCP/IP Illustrated, Vol. 1: The Protocols (Addison-Wesley Professional Computing Series)
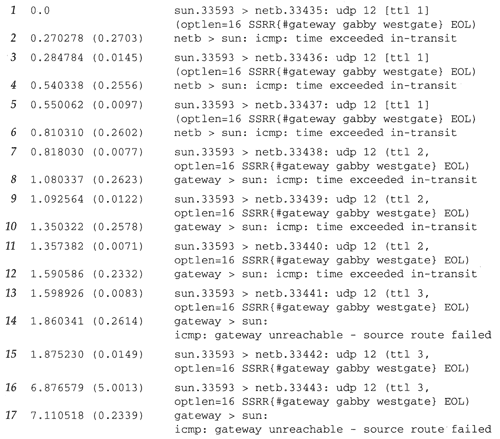
8.5 IP Source Routing Option | TCP/IP Illustrated, Vol. 1: The Protocols (Addison-Wesley Professional Computing Series)